FortiGate API
I don’t really do any automation or DevOps in my job but in the interests of tinkering I have got as far as writing a couple of FortiGate API scripts so I thought I’d share the process and scripts here.
The first script takes a backup of the FortiGate. It could be modified to encrypt the backup and then email it and I may well do that in subsequent versions. The script uses an embedded API token – which is not good practice so please bear this in my mind before deploying it anywhere. In my next post I plan to get this working with secrets (AWS or some roll your own option) . This podcast is a good listen on the alternatives available in this space.
Fortinet Developer Network
The Fortinet Developer Network is a portal which gives you details of all the API calls for Fortinet kit. To get a login, you need to request it from Fortinet themselves. I found it easy enough but then I work for a Fortinet partner which probably helped.
https://fndn.fortinet.net/index.php?/login/&ref=aHR0cHM6Ly9mbmRuLmZvcnRpbmV0Lm5ldA==
FortiGate API Administrator
To use API scripts, we need to create a RESP API Adminstrator on the firewall which is done in System/Administrators from the GUI:
Then define the administrator’s properties…
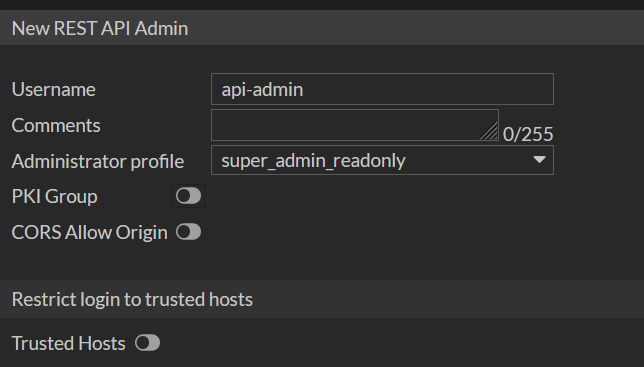
The PKI group is for certificate authentication which although a good idea will take some setting up. However, I would recommend inputting the ip address of the server(s) the script will be run from in ‘Trusted Hosts’ as this is an easy win.
When you complete the api admin creation you will be given the token to use for the access so take a copy of this.
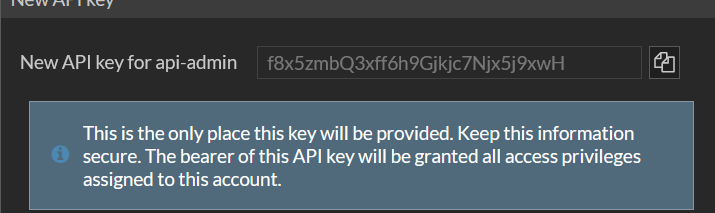
(Although, I created api-admin, here I use api-user in subsequent examples as I’d already created and tested this)
Admin Profile
Now, I found that to get a full backup configuration using the API admin it was necessary to use the highest level of profile access (super_admin). You cannot select this level of access from the GUI and need to amend it from the CLI. (This is another reason to secure this script.)
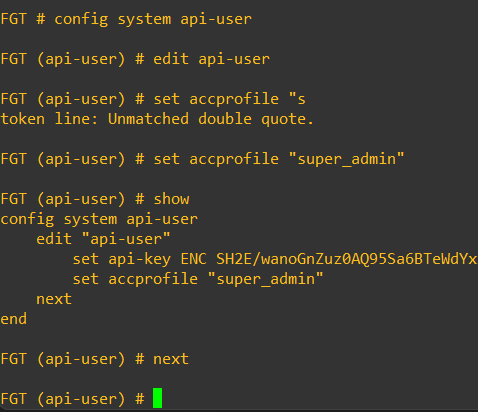
If you select a lower admin profile – the backup file will be created, but be incomplete. When I first wrote this on an older version of Forti code it just missed out sections with super_admin administrators but having re-tested it, I got a file with a 403 error in it.
The Script
You can access the REST API in a number of ways but I used a python3 script. The script has three variables.
firewall=”192.168.200.99″ # The address on fqdn on which to access the firewall.
fname=”FGT” # the firewall name used in the filename of the backup
api_token =”xxx” # As mentioned above, you probably shouldn’t be putting api tokens in scripts but this is a PoC.
The relevant parts of the script are:
api_url = “https://”+firewall+”/api/v2/monitor/system/config/backup?destination=file&file_format=fos&scope=global”
And the following which sends the HTTP GET:
response = requests.get(api_url,headers={“Content-Type”:”application/json”,”accept”:”application/json”,”Authorization”:”Bearer”+api_token},verify=False)
When this script is run it creates a backup file of the firewall in the same directory it is run from. The script can be found here…
https://github.com/tinkergar/fortiapi
This is incidentally my first upload to GitHub. It’s amazing how long you can be in this industry and still find yourself doing fairly fundamental things for the first time if you venture out of your silo. I blithely mentioned secret managers above, and although I know of them and have passed exams based on my so-say knowledge thereof I have never used them in anger. Every day’s a school day.