Cisco and non-std SSH
In a series only midly less compelling than GoT we see how the Cisco ASA firewall fared in stopping ssh over non-standard ports. (Spoiler alert: this lab did not go well)
SPOILER ALERT: I didn’t get this working and this post descends into a mild rant on ASAs in AWS. I did get it working in this post:
Cisco
Once again I headed to the AWS Marketplace to furnish myself with the appropriate vendor’s firewall and happened upon this one:
The ASA persists in using a Java client for GUI administration which I’ve always found a bit of pain to use. Why some vendors can run sophisticated GUIs in a browser but others rely on Java with its attendant annoyances of version compatibility, requirement for install (which in an enterprise environment can be a pain) and challenging security record, I don’t know.
Adding interfaces within AWS was painless with Palos and Fortis but seemed to require a reload on the ASA which took about ten minutes. I didn’t intend this to be a reivew of the various vendors offerings in AWS but we’re heading that way.
I’ve got the entry-level AWS ASA which only comes with a management interface. So I intended to add two more interfaces: an external and a DMZ one as in the previous lab. When I came to add the second I received this message:
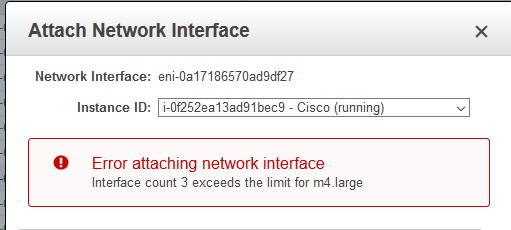
Er… so Cisco won’t let you have two interfaces on their AWS firewall. I decided to compare the instances I was using in AWS – maybe I was using some weirdly under-specced instance of the ASA. I decided to use price as the easiest means of comparison
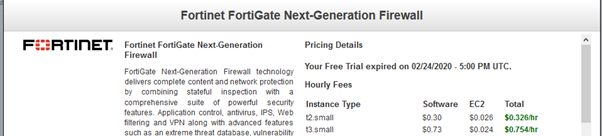
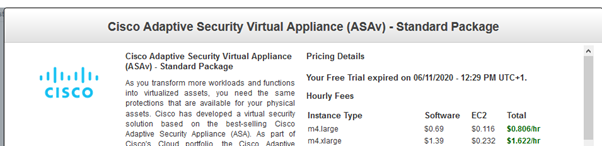
Ah, so the Forti run price is less than half that of the Cisco ASA. Hmmm.
OK, let’s work with what we’ve got. I remember there’s a setting on the ASA to allow the management interface to pass produciton traffic so I’ll remove the external interface from the ASA, just add the DMZ one and use the management interface for external traffic.
I tried to the remove the external interace (an easy operation on other vendors’ firewalls) and sat staring at this for five minutes.

OK, let’s chalk off another ten minutes of our lives and reboot. Having done this for some reason I couldn’t get back on to the firewall with either ssh or the GUI.
Right, well I hadn’t done too much on the instance so I terminated it and just fired up a new one and then added my DMZ interface. Yup, there it is showing on the instance.
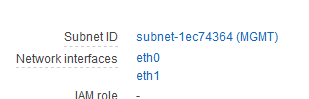
But not on the ASA itself.
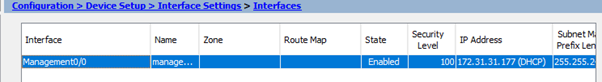
There may be something in the documentation that mentions you can’t do ‘hot’ interface additions / removals on the ASA in AWS. Anyway, another reboot later and finally we see two interfaces, the management interface and the DMZ interface.
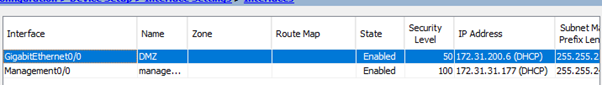
What were we doing? Oh yeah undedicating the management interface…

So let’s untick this… well to cut a long story short you can untick this little box and the command is accepted happily but when you try and add an access list to the management interface you have the following:
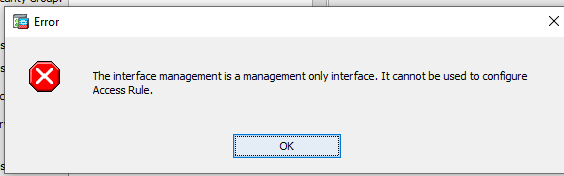
If you then go back and check the management interface the box next to ‘Dedicate this interface to management’ has magically re-appeared. They saw that one coming, eh?
Maybe, I could fire up a bigger instance but I can’t be bothered. I hereby disqualify the Cisco ASA from my non-std ssh test on account of it being too annoying to set up. I didn’t set out to do a hatchet job and I’ve spent a lot of time on ASA’s in the past and got a long with them fine so it’s more in sadness than anger (well, pique) that I do this.