Palo Alto and non-std SSH
Initially, I wanted to explore the ways that different models of Next Generation firewalls defeat (or not) the simple tunnelling scenario of the previous labs (see ‘SSH forwarding’).
In fact, I didn’t really get much further than looking at running applications on non-standard ports but it shows a little of the application awareness abilities of a next-gen firewall, in this case a Palo Alto.
As I didn’t have a physical Palo to hand the one I used is the model available in the AWS marketplace
(At first, I tied myself in knots setting this lab up in AWS after forgetting how routing works there and will maybe put together a note on this later )
For the firewall’s configuration, I tried to use as basic an out-of-the-box set-up as possible. The OS version in case you can’t see it above is 9.1.2
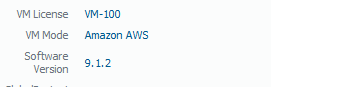
Going into the full configuration options on each model or vendor is beyond the scope of the this post so I will only touch on them where they are relevant to the scope of the lab.
The Lab setup is as follows…
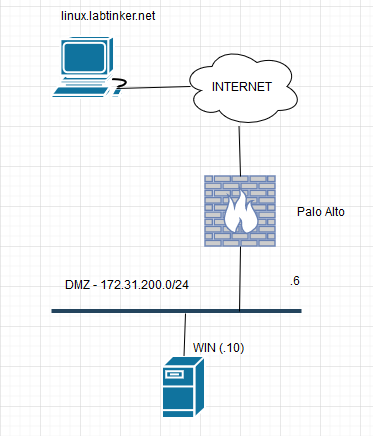
The Windows host is on a DMZ with an address of 172.31.200.10, the Linux host on the Internet and our trusty Palo sits between them. It is in turn is configured thusly:
We have a source NAT rule to hide our outbound traffic behind the firewall’s external interface in common with almost every firewall that connects to the Internet. The actual configuration is shown here:
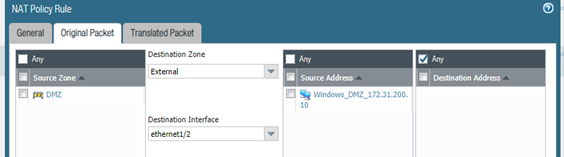
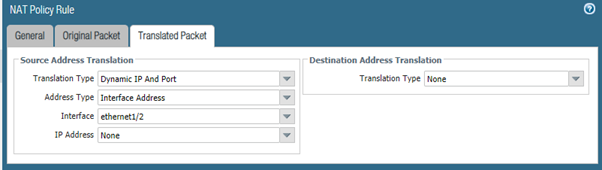
We have the following access rule named ‘Windows Out’ (for those without a magnifying glass) which is allowing any traffic out from the Windows Host on the DMZ zone to the External zone which leads to the Internet. This being a stateful firewall it will allow traffic back in if it is return traffic from the outbound session.

Tunnelling Out
The linux host linux.labtinker.net has an ssh listener listening on tcp port 80 which we will connect to from the Windows host as a precursor to tunnelling back in (spoiler alert – we’re not going to get as far as tunnelling back)
I’ve realised it is difficult to show the log screens in any detail so will capture the relevant bits… when our Windows host tried to ssh out to linux.labtinker.net on port 80 the traffic was denied.
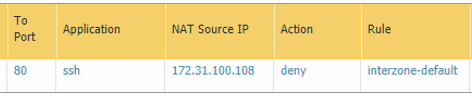
The log shows the traffic is hitting the ‘default’ deny rule and falling past our ‘Windows Out’ rule. It’s not immediately clear why this is as the source and destination ip addresses are both allowed by the ‘Windows Out’ rule.
However, in my rule I have selected any ‘application’ but not any ‘service’. The distinction is important.
I stipulated that any application should be allowed out. However, on a Palo the service (port) associated with an application is defined separately, and the default option for this setting is ‘application default’.
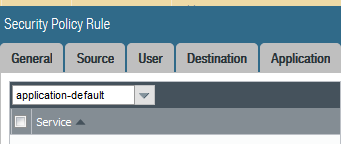
This means is that application traffic will only match the service portion of the rule if is using the application’s default port which for ssh is tcp 22, for http is 80 etc.
We were trying to use tcp port 80 for ssh which is not the default port for this application hence we fell foul of this part of the rule and our trafffic was blocked.
Let’s test this further in two ways: first by changing the ssh listener on linux.labtinker.net back to the standard tcp port 22 and trying to connect and secondly by reverting the ssh listener to port 80 and changing the Palo’s rule to allow the application to be accessed on any service (port) not just the default one.
Test One
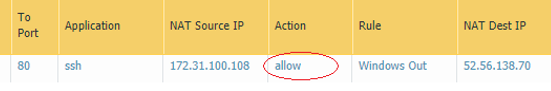
OK, Scout’s Honour, nothing changed on the rule but running the traffic over the correct port allowed it to sail through…
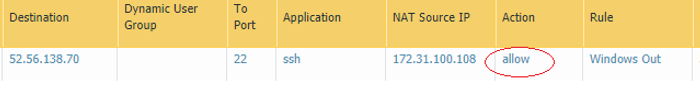
Test Two
And then changing the service in appropirate rule from ‘application default’ to ‘any’ and re-setting the ssh listener back to tcp port 80.

We are able to connect to linux.labtinker.net on ssh over tcp port 80
Applications not Ports
Palo Alto typically espouse using applications in the firewall’s rules rather than services (ports) but as has been demonstrated even if you do use services the ‘application-default’ settting would give you some protection.
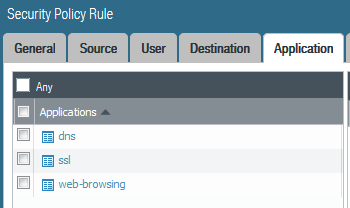
A best-practice Palo Alto rule to allow outbound browsing would use the application ‘web-browsing’ for clear text browsing in conjunction with application ‘ssl’ to allow https. (DNS would also be required but probably to specific destinations) – and of course the rule(s) would have ‘application-default’ specified for the service.
I didn’t get around to seeing if tunnelling back over ssh would work but then it seems a bit moot if you’re defeated getting out of the enterpise using a port that would be allowed (even the most slap-dash outfits wouldn’t allow port 22 out)
In the next couple of posts I’m going to compare a couple more NG firewalls and see how they fare in a similar set up.