As Easy as Falling of a Log
I encountered one of those smallish problems where I needed to do something slightly out of the ordinary and felt the need to share it here to spare someone a precious few moments re-inventing… not so much the wheel… as the perhaps the furry dice.
And so to the problem: I have/had an overly permissive rule on an ASA and after putting more granular rules above this I wanted a way of logging only what was still hitting the permissive rule. Lucky the ASA in question did/does not have syslog so the lab was to stand up a syslog server and configure an ASA to only log to the syslog server on a selected rule. (We’re not cracking the Enigma code here)
Back with GNS3 (I’m avoiding AWS for now after accidentally leaving a Cisco FMC and FTD turned on over the bank holiday weekend… that’s $150 I’ll never see again.)
So this is the set up:
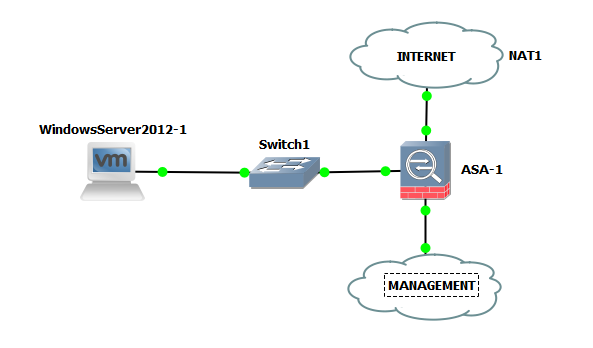
I downloaded Kiwi Syslog server (https://www.solarwinds.com/kiwi) and installed it on a Windows 2012 server VM. I initially got very frustrated in this lab because I couldn’t see any logs on my syslog console (despite checking I was listening on udp 514 and Wireshark traces confirming syslog was arriving). The next paragraph is a mild rant which you may want to skip.
This is what got me:
In Kiwi’s Setup menu, there is this ‘Inputs’ section
To me this menu looks like a title ‘Inputs’ and some options beneat, but the actually the ‘title’ itself is an option… that you need to click on – and it’s therein that you define the allowed hosts. (which is 10.10.10.99: the ASA’s inside interface)
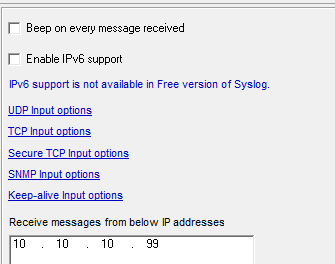
I scoured all the options several times before this occurred to me.
Rant over. And Kiwi / Solarwinds do provide the software free of charge… so beggars shouldn’t be critics (I paraphrase)
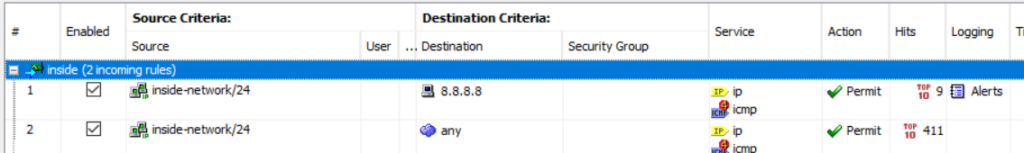
My approach was as follows. I have two rules – shown above. The first allows traffic from the Windows server to the ip address 8.8.8.8 (Google’s DNS) the second allows access to anywhere. I am logging on the first rule at ‘alert’ level and the second at ‘default’ level.
First rule logging details:
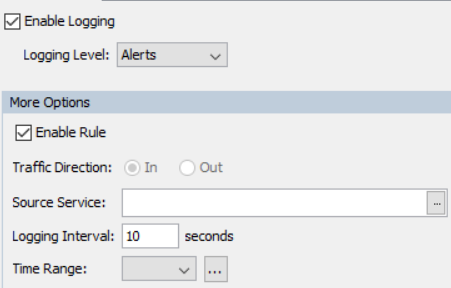
Second rule logging details:
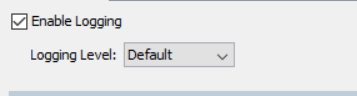
I have reduced the logging interval down from its default value of 300 seconds to 10 seconds for the purposes of the lab.
The above looks like this from the CLI.
access-list inside_access_in extended permit object-group DM_INLINE_PROTOCOL_2 10.10.10.0 255.255.255.0 object 8.8.8.8 log alerts interval 10
access-list inside_access_in extended permit object-group DM_INLINE_PROTOCOL_1 10.10.10.0 255.255.255.0 any
And this is the relevant bit of the ASA logging config…
ASA1# show run log
logging enable
logging timestamp
logging trap alerts <<< send ‘alert’ level logs to syslog
logging asdm informational
logging queue 8192
logging host inside 10.10.10.12 <<< Specify the address of the syslog server (The Windows 2012 server)
So from the Windows server if we ping 1.1.1.1 we should see nothing and yet when we ping 8.8.8.8 we should get logs.
Pinging 1.1.1.1 (notice the cmd box artfully placed over the syslog server display)
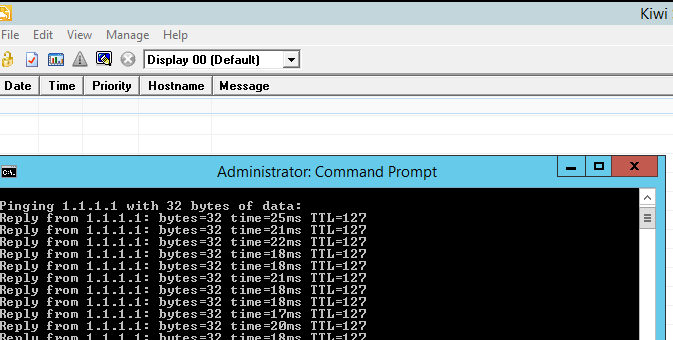
Not a scooby. And let’s try the same pinging 8.8.8.8
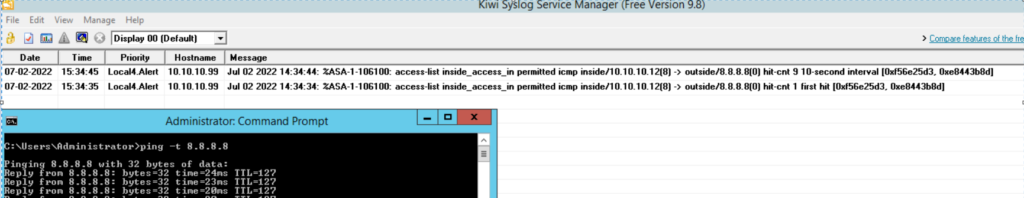
The syslog server logs this traffic these because the ASA logs these at ‘alert’ level which is the level of logs which it’s configured to send to the syslog server.