Call the DNS Doctor
I never really knew DNS doctoring was much of a thing until I encountered it: essentially getting your firewall to alter or doctor DNS responses. One use case for this might be that you can have your internal hosts receive an internal DNS address whilst keeping them pointing to an external ISP’s DNS. I could go on but somebody already has:
So I thought I would have a tinker. This is my set up in GNS3. A Linux host connecting to the Internet through an ASA which will be doing the doctoring….
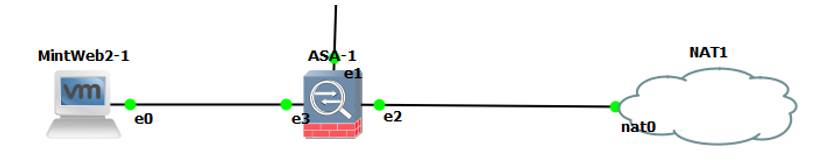
The ASA has the following interfaces:
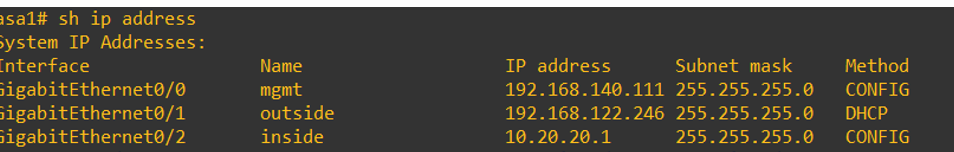
The linux host (MintWeb2-1) in on the inside interface of the ASA, the Internet is on the outside interface and the following NAT statements are in place:
nat (inside,outside) source dynamic any interface
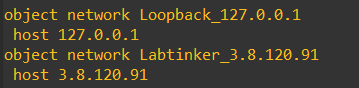
nat (inside,outside) source static Loopback_127.0.0.1 Labtinker_3.8.120.91 dns
(You can’t use addresses in the nat statement but have to use objects – thus I defined two host objects and named them with the addresses – to make it clear what’s going on)
This looks like this on the ASA’s ASDM GUI:
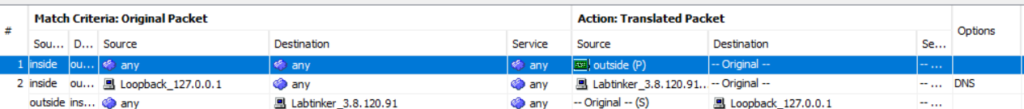
The first NAT statement is to PAT traffic to the Internet but the next one does the clever stuff. Essentially, it will alter any DNS responses containing the address 3.8.120.91 and replace said address with 127.0.0.1.
The Linux host is set up to get its DNS from the Internet DNS server(s) on 8.8.8.8 and so when it browses to www.labtinker.net, the Internet DNS will respond with an address of 3.8.120.91 but the ASA will intercept this response and change it to 127.0.01 (the host’s loopback address).
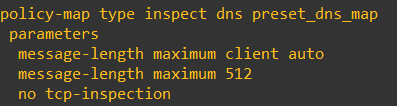
It should be noted, as mentioned in the explanatory link abov, that you need dns inspection defined on your ASA for this to work (it should be set up by default)
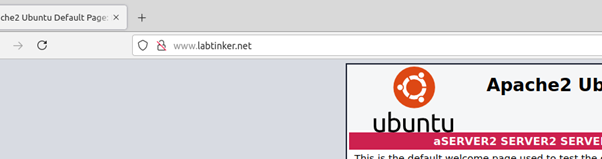
And well, dear reader, it works… From the Linux host I browsed out to www.labtinker.net which and was re-directed to the webserver on the host’s own loopback address: (127.0.0.1).
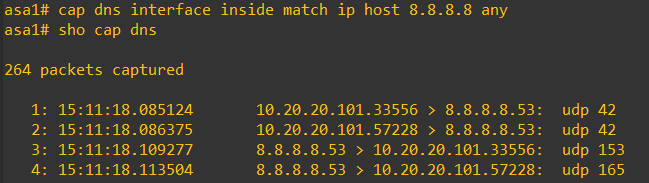
To see the DNS doctoring working on the ASA I did the following: Set up a capture to 8.8.8.8
Cleared the DNS cache:
And then browsed out again to www.labtinker.net
There are various ways to get a pcap of the capture from the ASA but one is:
https://<ip_of_asa>/admin/capture/<capture_name>/pcap
Which in my case is:
https://192.168.140.111/admin/capture/dns/pcap
(You have to authenticate with the ASA)
You may want to rename the pcap but after opening it with Wireshark we can see the traffic and begin looking out for dns address responses…
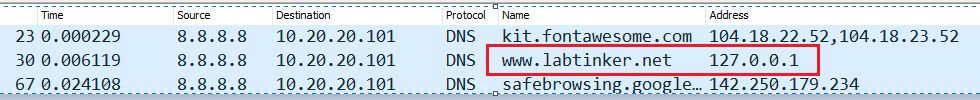
(I added a column in Wireshark for the DNS address response or you can find a DNS address response in the trace and just add it as a column)

And then sorting on this field and looking for 127.0.0.1 lo and behold:
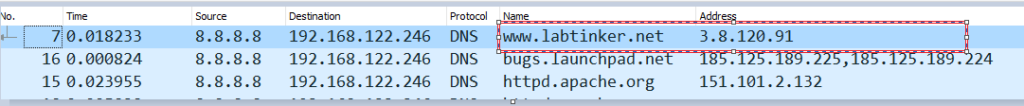
I repeated the capture on the outside interface where I expected the original address to seen in the DNS response and indeed it was…
The doctor is now getting himself a beer (me, not the firewall).