Licence Revoked
Apparently the Bond film ‘Licence to Kill’ was originally going to be called ‘Licence Revoked’ but the producers were worried that the general public wouldn’t know what ‘revoked’ meant. (The use of ‘apparently’ in this sentence denotes a lack of fact checking).
To revoke means to withdraw or cancel and in TLS, certificate revocation is the mechanism by which the owner of a certificate can let the world know that a certificate should no longer be trusted. There are three ways a client can check whether a certificate has been revoked:
Certificate Revocation Lists (CRLs)
There are URLs contained within a TLS certificate which tell the client where to download a list of certificate serial numbers of revoked certificates. To check whether a certificate has been revoked a client (usually a browser) downloads this list (which can be thousands of lines) and reads through it to see if the serial number of the relevant certificate is there. Strictly speaking it needs to do this for the certificate’s root and intermediate certificates too. It is very time consuming and modern browsers don’t like the latency this entails.
Onilne Certificate Status Procotol
Contained with the TLS cert is the address of an OCSP Responder which the client can query using OCSP to find out whether the certificate has been revoked. The Responder will reply with a response (signed by the Certificate Authority).
OCSP Stapling
Similar to the above but the server hosting the certificate makes queries to the Certificate Authority’s OCSP responder at pre-determined intervals for the certificate’s revocation status and passes a time-stamped response to the client (if queried).
The Lab
My idea was a simple one: mint a certificate then revoke it and see how long it takes three different browsers: (Mozilla, Edge and Chrome) to notice.
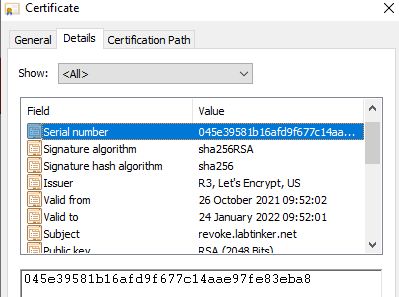
The certificate in question was revoke.labtinker.net issued by Let’s Encrypt:
I span up a Linux box with an Apache webserver on it and attached the certificate to it:
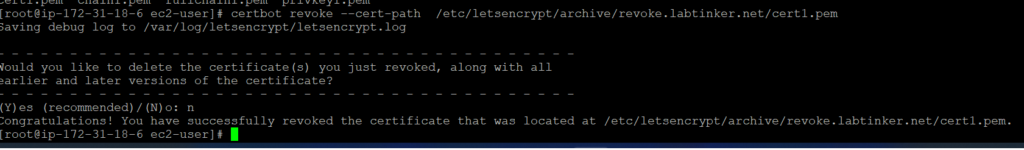
I then revoked the certificate via the certbot utility (which I’d used to provision the cert too)
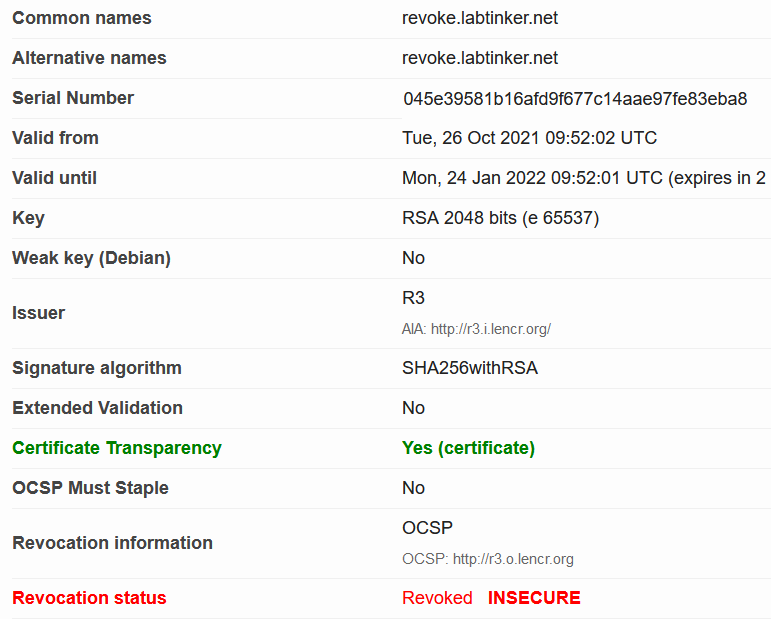
I checked in SSL labs (https://www.ssllabs.com/ssltest/) that it had been revoked:
I then tried to browse to the site using Mozilla (version 93.0) Edge (Version 95.0.1020.40) and Chrome (Version 95.0.4638.69) .
It was about thirty minutes after I’d revoked the certificate that I made my first attempt and Mozilla immediately detected that the certificate had been revoked:
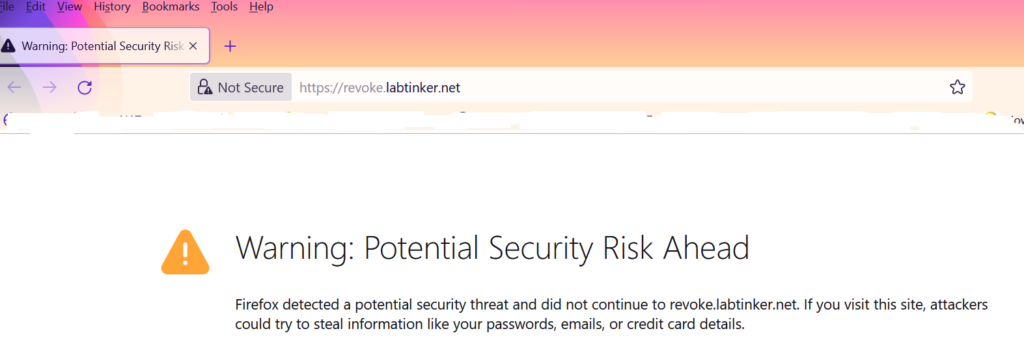
It had detected this by using OCSP to make a query to the OCSP responder URL published in the cert:
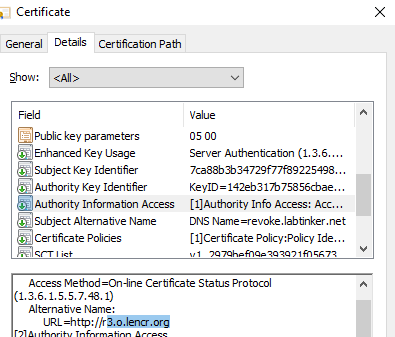
…as can be seen in the Wireshark capture below. Here’s the OCSP request:
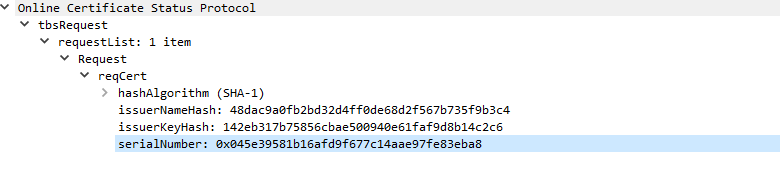
And here’s the response…
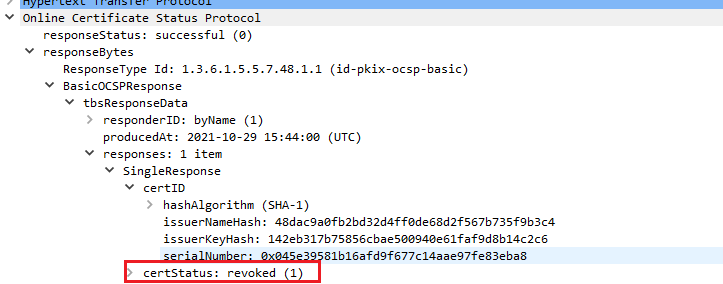
Excellent. Full marks to Mozilla.
I tried Edge and Chrome and received no warnings. I tried six hours later. Same. I tried thirty six hours later and still no warnings. These browsers do have their own mechanisms for doing revocation (beyond the scope of this lab) but they weren’t effective to get a pass here. (You can also modify these browsers’ settings to change revocation-checking behaviour – I was using vanilla settings)
Returning to the tenuous conceit of the post, in the above instance only Mozilla would be asking 007 for his licence and gun back!
Mozilla will actually soft-fail – which means if it doesn’t get a response from the OCSP responder it will allow access to the site. A summary of how different browsers deal with revoked certificates is here: