SAML Follow Up
The eagle-eyed amongst you may have noticed I used the certificate vpn.labtinker.net whilst running my Palo on the URL vpn.badtinker.net. The SAML authentication still worked because I guess the relevant public certs are in the metadata so no PKI checking; not in my set up anyway. I did eventually configure the correct certificate but the only difference it made was removing the browser warning I’d been happily clicking through when browsing to the Palo.
The tool I used when troubleshooting was the Chrome plugin ‘SAML tracer’ so here’s an excerpt of what I saw in that. (I did actually use system messages on the Palo as well.)
This is the SAML tracer output having got as far as the re-direct to the login screen of fs.labtiner.net. The entries with SAML related content are helpfuly highlighted in orange.
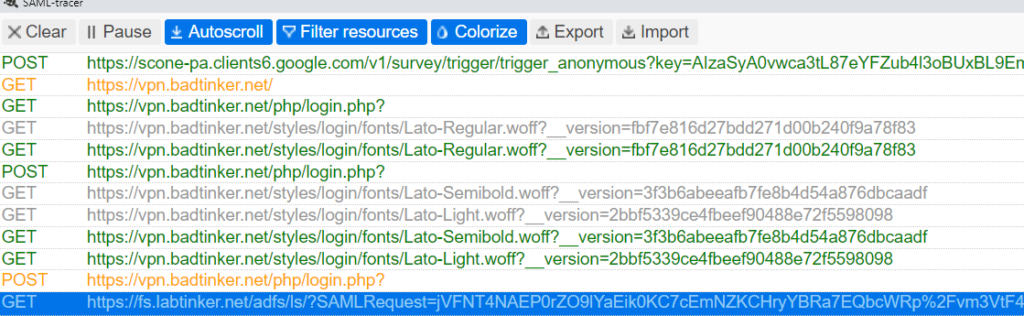
In the lower window you have the SAML info…
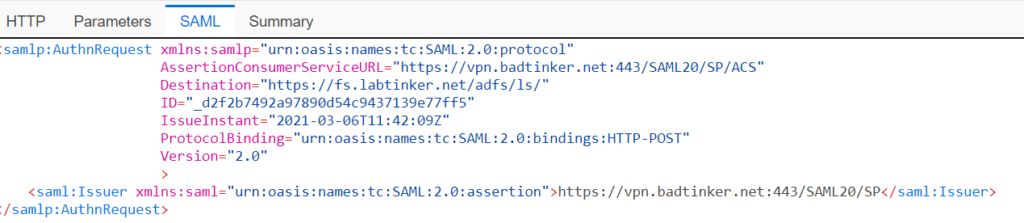
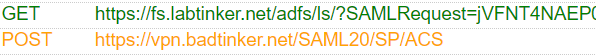
Having put in the password in fs.labtinker.net this is the return POST back to the Palo.
I’ve split the SAML response up into parts to make it more digestible. The first part of the response includes the destination….
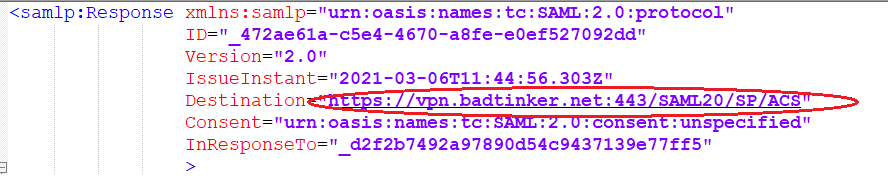
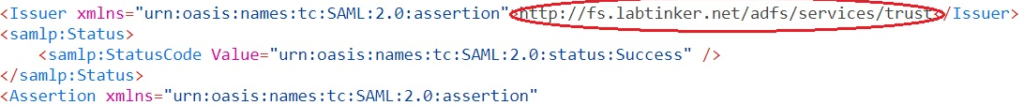
The second part includes the issuer id and also begins the actual assertion:
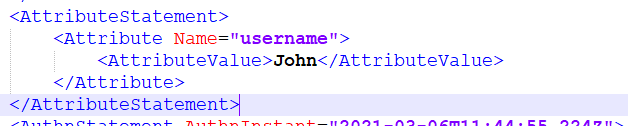
This includes details on transforms and methods used, the issuer’s signature and there at the bottom are the actual attributes of the assertion that the ADFS has passed on, in this instance just one: ‘username’: