It’s raining LSAs.
I generally work with security devices and my knowledge on routing protocols gets rusty as I don’t do much with them. However, we’re all supposed to be full-spectrum engineers these days which was brought home to me when I went to an interview a couple of years ago and was asked some questions in this arena…and ummed and arred. Anyways, long story short, to refresh my knowledge I did some dabbling with OSPF and BGP and came up with a lab to catch every(ish) type of OSPF LSA .
Every router that connects to a given OSPF area should learn the same topology from multiple LSAs (Link State Advertisements) which are multicast from other routers. This information is then stored in a LSDB. (Link State Database). The LSAs come in different types roughly summarised as follows:
LSA Types
- Router
- Network
- Net-Summary (ABRs – defines links and subnets)
- ASBR Summary – advertises host route to reach ASBR
- AS External
- Group Membership for MOSPF
- NSSA External
- Link LSAs
- Intra-Area prefix
This is the lab topology (running in GNS3) with mutliple routers running Cisco IOSv image. It was adapted to do other things as well as I recall so it’s bigger (and smaller – more later) than it needs to be. Also the ‘BGP Areas’ should really be labelled ‘BGP Autonomous Systems’ – I only noticed this mistake after I’d torn the lab down.
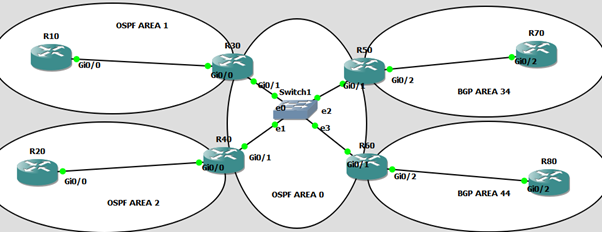
All the routers have loopbacks with ip addresses based on their name: R10 has 1.1.1.1, R20 has 2.2.2.2 etc.
The other interfaces are addressed: 192.168.<area>.<loopback last octet> so R10’s Gi0/0 interace is addressed 192.68.1.1.
LSA Type 1-5
An LSA Type 1 is the router advertising itself. Let’s choose a connection between any two routers running OSPF and capture the packets between them using Wireshark. (You can use ‘show ip ospf database’ on the router to get an idea of the LSA’s received but I prefer to see them on the wire.)
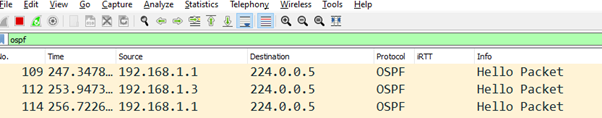
At first, I just saw lots of OSPF hellos as this needy little protocol reassures its neighbours that it’s still there:
So we probably need to prod something to trigger some updates…
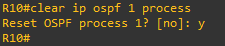
Doing this generated a lot of interesting new traffic. Wireshark has some display filters which correspond to our LSA types by name,the first being ospf.lsa.router.
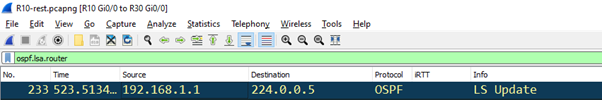
We’ve bagged an LSA type 1.
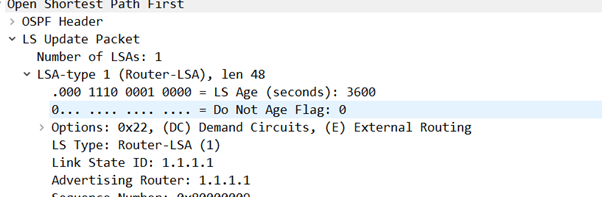
I won’t go overboard on detail on what all these LSA’s do because this man has…
…but essentially the router is adverting its own interfaces…
Onwards and upwards, let’s try ospf.lsa.network in the Wireshark filter window…
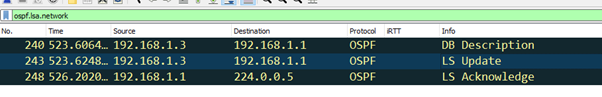
Got one. In fact, this LS Update contains multiple LSA Types. It has a LSA Type-1 and also…
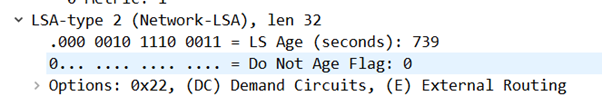
…which is generated by the designated router for the Area (R30 – OSPF id 3.3.3.3)
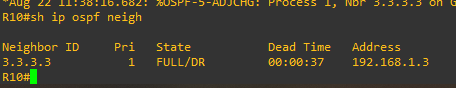
…and also tucked away in there is….
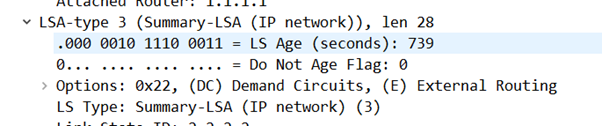
LSA Type 3s are generated by ABRs which straddle two OSPF areas and as R30 straddles Area 1 and Area 0 that makes sense. But we’re not finished yet…
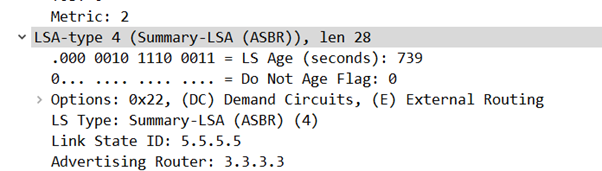
LSA Type 4s advertise the presence of as ASBR (Autonomous System Border Router) which covers R50 and R60 as they’re re-distributing BGP. And is there more…
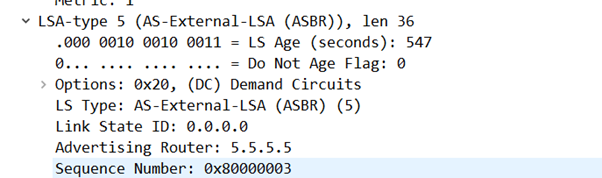
Again from the ASBRs advertising externally re-disributed routes. (Seriously, read the link above as I know my explanations are sketchy)
OK let’s excuse ourselves from looking for Type 6s as these are for multicast OSPF, not widely used, nor apparently supported by Cisco. Which just leaves us Type 7s (there are more types but they’re for more abstruse purposes and beyond the scope of this post)
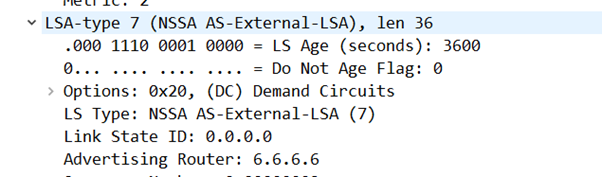
LSA Type 7s
Now these are a rarer beast – and the lab will need a little jerry-rigging to catch one
LSA Type 7s are created by ASBRs to inject into an NSSA (Not-So Stubby Areas). Our current ASBRs are on the edge of Area 0 – and as Area 0 rules and connects to all other areas it cannot be an NSSA. So we’re going to have to latch a new area on.
Now as I was doing this it occurred to me I was also a little shaky on the difference between stubby and NSSA. One google search took me here:
https://community.cisco.com/t5/switching/difference-between-ospf-stub-and-nssa-area/td-p/945048
Essentially, it’s a a stub as far as OSPF is concerned but is allowed to connect to the outside world.
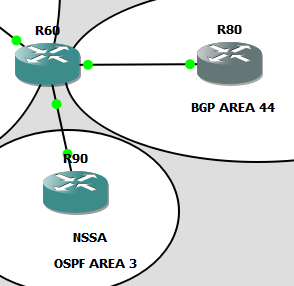
I updated the OPSF config as follows on R60.
router-id 6.6.6.6
area 3 nssa default-information-originate
network 6.6.6.0 0.0.0.255 area 0
network 192.168.0.0 0.0.0.255 area 0
network 192.168.3.0 0.0.0.255 area 3
default-information originate
And on R90 it was all new
router ospf 1
router-id 9.9.9.9
area 3 nssa
network 9.9.9.0 0.0.0.255 area 3
network 192.168.3.0 0.0.0.255 area 3
And then re-setting the ospf process as above…
Here are the configs if you’re interested. Apologies, my WordPress console won’t allow zips: